In the past, we’ve recommended keeping your smart gadgets simple. If you put sensitive devices onto the cloud (such as CCTV cameras), outside agents can access and use these devices.
Stuff like smart bulbs, however, seemed too simple for a hacker to manipulate in a devastating way. A recent report from Check Point, however, has discovered a nasty exploit within Philips Hue which shows that even light bulbs are a nasty threat in the IoT world.
How Does The Attack Work?
To begin the attack, the hacker plants some malicious firmware onto the bulb itself. For the attack to take place, however, the victim has to disconnect and reconnect the bulb via the app. The hacker, therefore, needs to “encourage” the victim to do this.
First, the hacker takes control of the bulb’s color and hue, locking the victim out. Then, the hacker will modify the light to give it the impression that it has suffered a glitch. For example, they may dim the light considerably and lock it into one color.
The user then tries to fix the bulb on the app, but it doesn’t respond due to the hacker’s interference. The user checks their bulbs and finds that the glitching one is labeled as unresponsive. The user then decides to disconnect and reconnect the bulb to fix this.
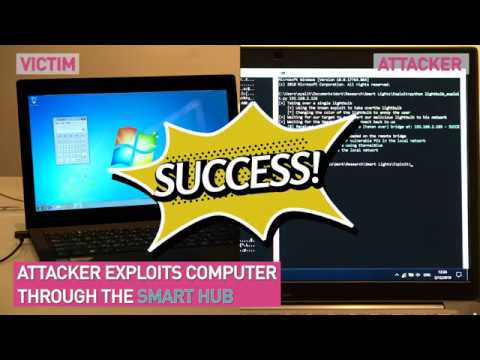
When the user reconnects to the bulb, the compromised firmware can do its job. It grants the hacker access to the user’s smart hub, where they can perform far more serious damage than before.
How to Protect Against This Attack
Fortunately, Philips Hues bought recently don’t have this vulnerability. If you bought your bulbs a while ago, Philips has since released a firmware update that patches this problem. As such, be sure to update your firmware to ensure that hackers can’t sneak in.

This attack shows how important it is to keep your devices updated. As Yaniv Balmas, the Head of Cyber Research at Check Point Research put it:
“It’s critical that organisations and individuals protect themselves against these possible attacks by updating their devices with the latest patches and separating them from other machines on their networks, to limit the possible spread of malware. In today’s complex fifth-generation attack landscape, we cannot afford to overlook the security of anything that is connected to our networks.”
However, this bulb hack is a good example of how intelligent these attacks are getting. Protecting yourself from this problem isn’t as easy as downloading a program or using common sense, as this attack is meant to look like the bulb is glitching.
As such, the best defense for this kind of attack is to follow the advice that Yaniv gave above. Never put sensitive gadgets on the same network as IoT devices that can be hacked. If someone does manage to infiltrate your IoT system, they will have mundane devices to play with instead of your personal information. Also, it will be even better if you can get smart devices that doesn’t require internet connection.
Keeping the Lights On
At first, recommending IoT devices like smart bulbs seemed like a safe bet. After all, what can a hacker do with a light bulb? As it turns out, they can do quite a lot; so much so that it’s worth putting seemingly-benign devices on their own network.
Does this put you off purchasing smart lights? Let us know below.