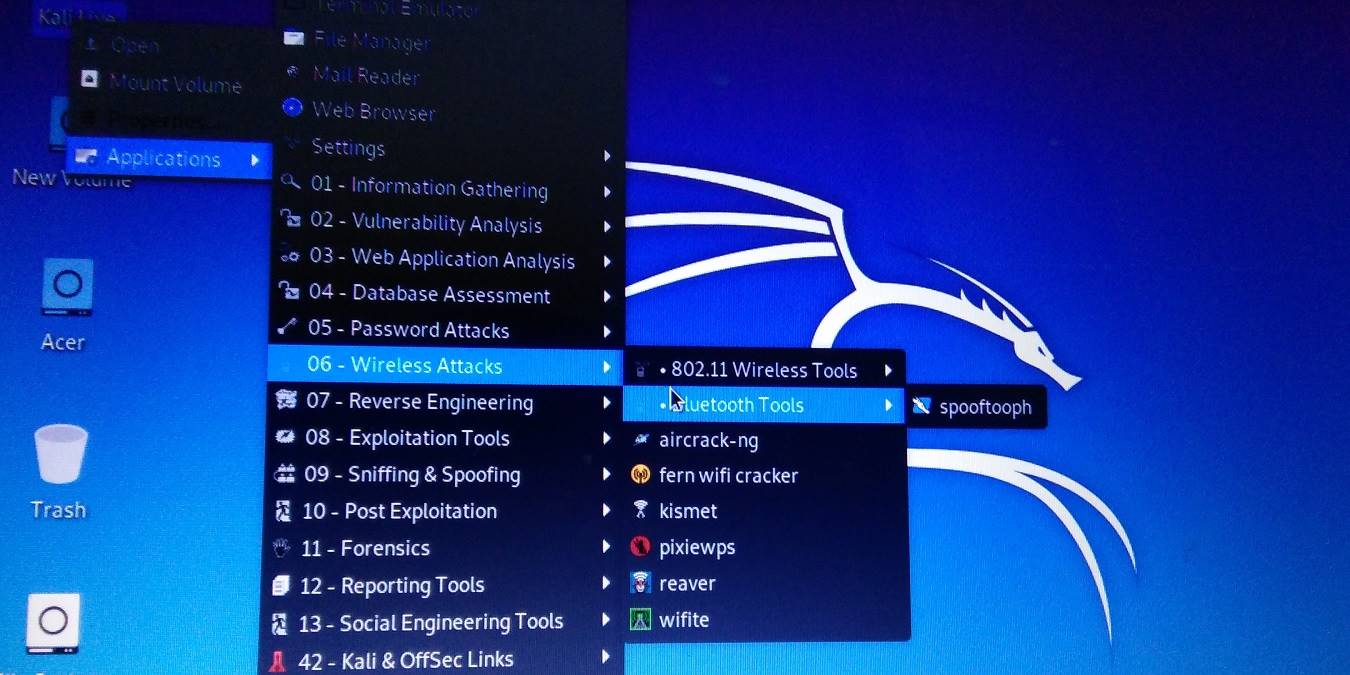
Kali Linux can be used to perform a variety of penetration tests on your computer in conjunction with other related techniques.
With an overall security strategy involving device-specific operating systems, firmware, and network configurations, it can serve as one of the penetration tools to target Internet-enabled smart devices.
Once you learn how to work with Kali Linux, you will find it helpful to cross-check your IoT network and its devices for potential vulnerabilities, exploits, sniffing and spoofing attacks, password attacks, social engineering attacks, and more.
Laid out here is the background and methods of a penetration testing strategy for IoT devices involving Kali Linux.
How to Get Started with Kali Linux?
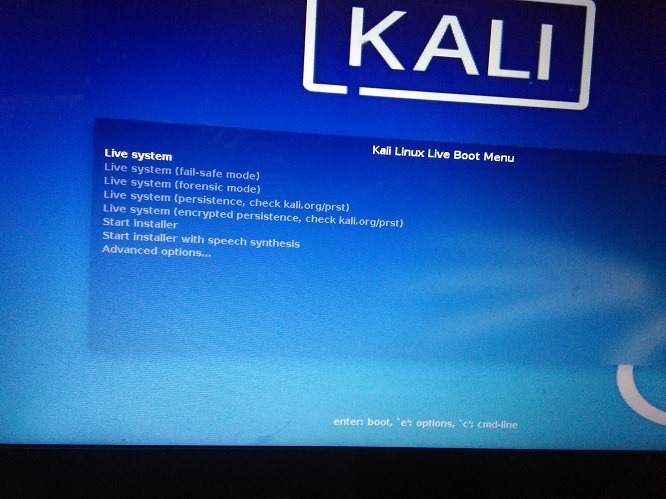
To begin, you will need to have Kali Linux installed on your PC or a bootable USB drive with the Kali Linux ISO etched on it. On Windows systems, you can boot the Kali Linux GUI from the “Advanced startup” menu followed by selecting the USB/EFI mode.
The first homescreen will give you a number of start options. Select “Live system (forensic mode)” to boot your PC into Kali Linux.
It takes a couple of minutes for the GUI to display on the screen. Many of the penetration tool options are available from them “Kali Live” menu which leads to a terminal as shown here.
To know the commands for any attack, you can find a comprehensive listing of Kali Linux penetration testing tools at this link. The same instructions are repeated in the terminal.
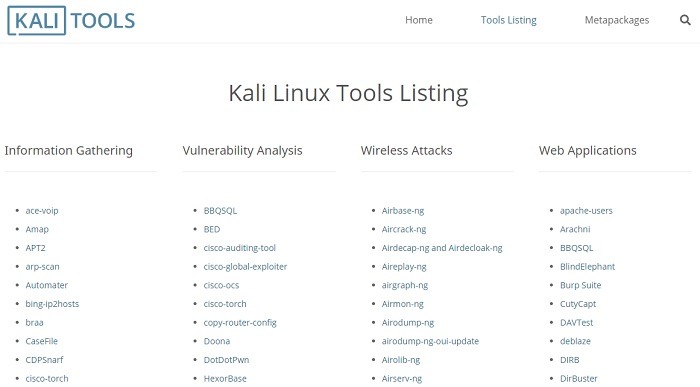
There are also stress testing tools, password attacks, exploitation tools for backdoors, trojans, router exploits, IP address forging, phishing attacks, and DNS tracing.
Discussing a General Penetrating Strategy for IoT Devices
Unlike Internet-enabled computers, penetration testing for IoT devices has multiple barriers. There is not just a Wi-Fi home network to break into. You need the exploits to work on BLE, Zigbee, LoRaWAN, MQTT, and many other networks where the device operates.
Then there are multiple parts of the hardware which can be targeted: chips, sensors, cameras, APIs, and more. The hacker or pen tester has to be able to target the device’s firmware or operating system.

This makes the penetration testing more multifarious and difficult. However, as a side benefit, it should be as elusive for the hackers as well. But some smart devices may be hiding a major vulnerability that can be exploited using a penetration tool like Kali Linux.
As recently as two to three weeks ago, the Ring Doorbell was in the news for device hijacks, multiple suspicious login attempts and even hackers creating their own podcasts over hacked Ring footage.
According to a spokesperson for the Ring team, these attacks occurred because the device owners had not enabled two-factor authentication (2FA) and were using very simple passwords which can be found in hacker metasploit databases.

How to do Penetration Testing for IoT Devices?
Using the above cue, let’s design a strategy to penetrate a video doorbell device which comes shipped with easy passwords or one in which the owner has set easy passwords with no two-factor authentication.
This trick will be assuming that the smart device is a metasploitable machine whose IP address has been known through someone having access to the network remotely. For more details on how metasploits are used to access weak hardware, check this link.
We will use a very common online password attack for Kali Linux called Hydra. In this attack the login cracker uses an extremely large database of stored passwords to penetrate devices with weak passwords.
Use the command as per the stored location of the metasploit file to try and recover the password from an unsecure device.
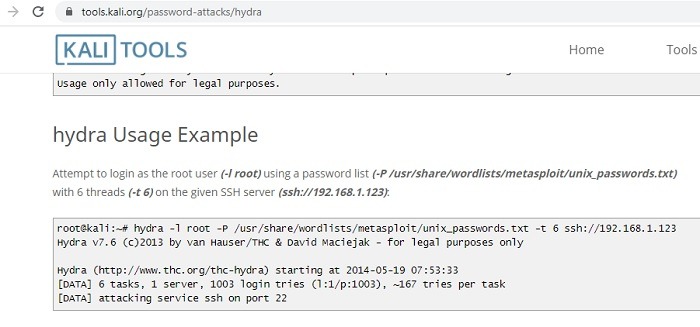
You need to go to the relevant folder where the passwords have been stored for metasploit. In my case, I stored it in a folder for user/share/wordlists.
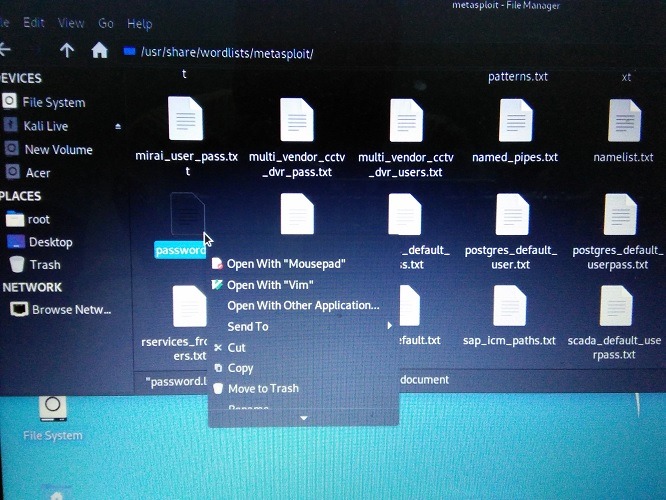
It has a large collection of stored passwords. One of them will be displayed if there is a match with the penetration testing of Hydra tool.
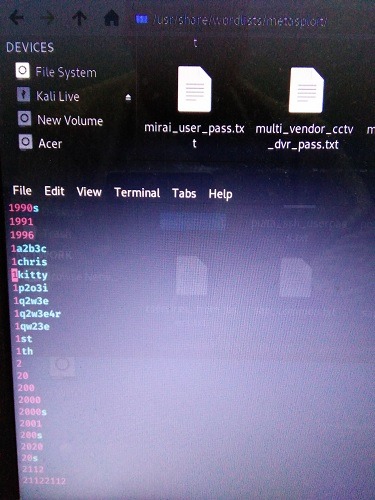
The brute force methods should definitely work with IoT devices which are shipped with factory passwords that never change. According to Trend Micro, they had to block over five million camera hack attempts due to brute password guessing.
Conclusion
If you have started working with Kali Linux, you might find yourself with the ability to get into the minds of hackers. Apart from the 600+ regular hacks and exploits featured on the Kali website, you can find many other third-party references as we saw with the video doorbell example.
Will you feel more secure using smart devices if you had an advanced penetration tool like Kali Linux at your disposal? Do let us know in the comments.